So iv have created the app and i want to test it’s security can you please find api key
https://drive.google.com/drive/folders/12dT5bVvaSN3sxdhgK1VH0_0o45oiZBEe
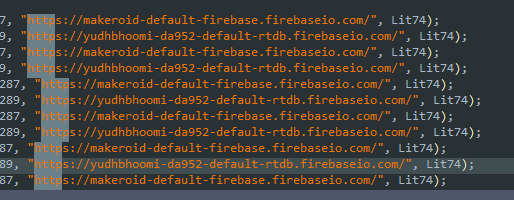
Note thare is two api key two firebase url
One is fake for fool hackers
so lets find out and let me know
@nikzdevz Can you store values in database please
No, sorry i’m not gonna do that.
Your token may be something like this
AIzaSyCxfHY******************
I can’t paste complete token..
@nikzdevz i think you cant find api key i said find api key and store values
no that is fake token find real token please
Okay now i’m leaving the topic.
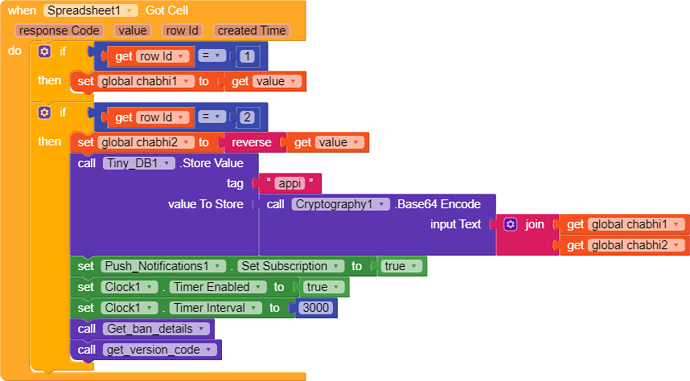
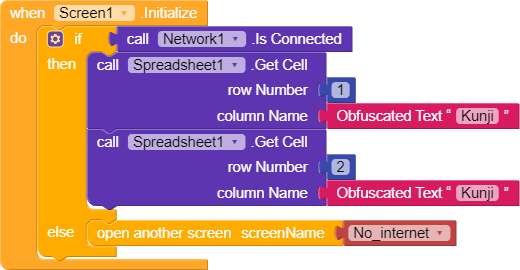
Also a feedback app is not secure use obfuscate block to make your key and url little bit secure.
And I am not going to store any value as don’t want to much into this topic.
ok you won but can tell \me how to secure it more
Thanks
Already told here
@nikzdevz it mean i have to use url in obfuscate block how can i secure api more better which extension is best
If you can create own encryption it will be best else use kodular’s obfuscation or any encryption extensio
@nikzdevz can you find airtable api key also?
Please tell me
@All_In_Hindi it is possible to find airtable key
@HritikR What will happen if example my api is dogcattiger128 and i store value in airtable is dogcattigeur128 after i got value i will erase u and use it as api key ?
If you will erase the value from airtable. How will other users get that API key stored in airtable?
@HritikR for example my firebase api key is “lokiee” and i stored “lokfiee” and when got value i will erase “f” after that i will use it is this good?
https://www.youtube.com/channel/UC1O_ZmA-pbhOwsoibHSH7vg
https://yudhbhoomi-da952-default-rtdb.firebaseio.com
https://yudhbhoomi-da952-default-rtdb.firebaseio.com/
https://yudhbhoomi-da952-default-rtdb.firebaseio.com/Appdetails
https://yudhbhoomi-da952-default-rtdb.firebaseio.com/Join
https://yudhbhoomi-da952-default-rtdb.firebaseio.com/Numbers
https://yudhbhoomioffical.blogspot.com/2022/01/yudhbhoomi-home-page.html
https://drive.google.com/drive/folders/1fwWMDx6YK8B3nGcZcsrMVasNM7MqpTOc?usp=sharing
https://drive.google.com/file/d/1LeqhLTxNefQJUF3yeK4clDoufptCXxSQ/view?usp=drivesdk
I got onesignal and firebase API key and i was able to bypass the screen and able to edit tiny db values on rooted device and i changed the app package name by modifying the Dex files and app still works without checking package name and i got some obfuscated strings and these obfuscated strings values was readable at run time by reading memory and traffic capture
which software did you use